In today’s digital age, the adoption of cloud computing has revolutionized the way businesses store, manage, and process data. However, as organizations increasingly rely on cloud services, data security in cloud computing has become a critical concern. This article delves into the key aspects of ensuring security and privacy in cloud environments, offering insights into best practices, challenges, and solutions.
Understanding Data Privacy in Cloud Computing
Data privacy in cloud computing refers to the measures and practices that protect sensitive information from unauthorized access, misuse, or breaches. Cloud platforms often store vast amounts of personal and business data, making them prime targets for cyberattacks. Ensuring security and privacy in cloud computing requires robust mechanisms to safeguard both the data in transit and at rest.
Key Threats to Data Security in Cloud Computing
- Data Breaches: Unauthorized access to sensitive information stored in the cloud.
- Data Loss: Accidental deletion or corruption of data, emphasizing the need for data loss prevention in cloud computing.
- Insider Threats: Malicious or negligent actions by employees or contractors.
- Weak Access Controls: Inadequate authentication mechanisms can compromise database security in cloud computing.
Addressing these threats requires a combination of cloud-based data protection technologies and robust policies.
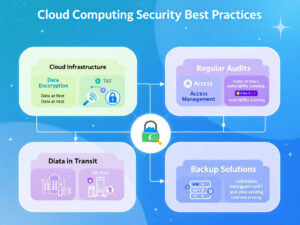
Cloud Computing Security Best Practices
To enhance cloud computing and data protection, businesses should follow these best practices:
- Data Encryption: Encrypt data both in transit and at rest to ensure data privacy in cloud computing.
- Regular Audits: Conduct frequent security assessments to identify vulnerabilities.
- Access Management: Implement strict access controls and role-based permissions.
- Backup Solutions: Use automated backups to prevent data loss, ensuring effective cloud protect mechanisms.
By adhering to these cloud computing security best practices, organizations can significantly reduce their risk profile.
Tools and Technologies for Data Protection in Cloud Computing
Modern tools designed for data protection in cloud computing include:
- Firewalls and Intrusion Detection Systems: These protect against unauthorized access.
- Identity and Access Management (IAM): Critical for managing user permissions.
- Secure APIs: Essential for protecting applications interacting with cloud database security.
- Data Loss Prevention (DLP) Solutions: These tools monitor and protect sensitive data, ensuring data loss prevention in cloud computing.
The Role of IT Security in Cloud Computing
IT security cloud computing involves implementing technical and organizational measures to secure cloud infrastructure. It’s essential for organizations to work closely with their cloud service providers to establish shared responsibility models that define who is accountable for various aspects of data security and cloud computing.
Emerging Trends in Cyber Cloud Security
- Zero Trust Architecture: A “trust but verify” approach to enhance security and privacy in cloud computing.
- AI-Powered Security: Artificial intelligence tools for detecting anomalies and preventing breaches.
- Hybrid Cloud Security: Integrating security solutions across public and private clouds.
These trends underline the importance of staying ahead in the evolving landscape of cyber cloud security.
Future of Cloud Database Security
As cloud computing continues to grow, ensuring data security in cloud computing will remain a top priority. Organizations must invest in robust security frameworks, leverage cloud-based data protection solutions, and adopt a proactive approach to cloud computing and data protection. By doing so, they can build trust with their stakeholders while safeguarding critical information.
Data protection in cloud computing is not just a technical necessity but a business imperative. Embracing cloud computing security best practices and staying informed about the latest trends will enable businesses to thrive in the digital era.







No comments yet. Be the first to share your thoughts!